Kubernetes WAAP Version 1.16.0
This version includes the following new capabilities:
Actor Anomalies
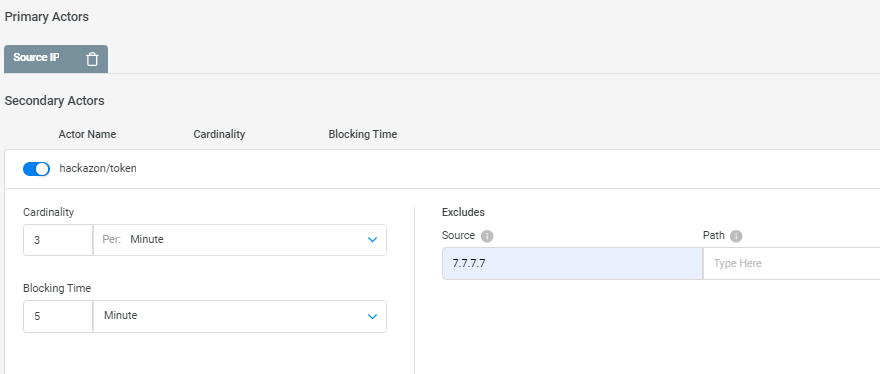
The Actor Anomalies protection introduces advanced detection capabilities to identify potential security threats associated with HTTP transactions involving multiple actors.
Some key points of this functionality:
 Actor Anomalies Detection
Actor Anomalies Detection—The protection identifies cases where a single HTTP transaction is linked to two or more actors which signals a potential anomaly.
 Anomaly Scenarios
Anomaly Scenarios—For instance, if a logged-in user is accessing the application from more than 5 different source IPs within the same hour, it could indicate compromised credentials. This proactive detection helps thwart potential security breaches where bots attempt to scrape data without triggering traditional quota or surge protections.
 Customizable Protection
Customizable Protection—Actor Anomalies protection allows you to define a primary actor (for example, username obtained via a JWT claim) and a secondary actor (for example, source IP). By setting specific thresholds for the combination of these actors, you can control the allowed changes over a desired time frame.
 Blocking Mechanism
Blocking Mechanism—If an HTTP request contains both primary and secondary actors, and the combination is altered for the secondary actor more than the defined threshold within the specified time frame, the primary actor is automatically blocked for a designated blocking time.
 Exclude
Exclude—There is an option to add an exclude rule to the primary actor based on source and path.
Security Inspection Latency Control
The Security Inspection Latency Control feature empowers you with the ability to fine‑tune and balance the trade-off between security and user experience by defining maximum inspection times for various request protections such as signatures, expressions, and patterns.
Some key points of this functionality:
 Customizable Max Latency Time
Customizable Max Latency Time—By setting the maximum time limit, in milliseconds, you can control the time spent on inspecting requests while maintaining a balance between security levels and usability.
 Priority and Weight Configuration
Priority and Weight Configuration—Define the priority for the ordering of protections to ensure the desired sequence of execution. Assign weights to protections as a percentage of the maximum time to enable allocating inspection time proportionally.
 Flexible Activation
Flexible Activation—Max Latency Control is disabled by default for seamless deployment. You can activate the feature during each Enforcer deployment in accordance with their security policies.
 Automatic Protection Termination
Automatic Protection Termination—If a protection task exceeds its allocated time, it is automatically halted. Access logs provide clear indications of incomplete protections which facilitates analysis and troubleshooting.
Client Request Decompression
Client Request Decompression supports various compression methods in HTTP requests to enhance data transfer efficiency. With this feature, you can now configure KWAAP to handle compressed (encoded) content requests. The decompression capability allows you to fine-tune parameters and thus ensure optimal decompression of data before processing requests.
The following compression methods are available:
 Gzip
Gzip—Widely utilized for compressing text-based data such as HTML, CSS, and JavaScript files. This is supported by the majority of web browsers and web servers.
 Deflate
Deflate—Another compression method for text-based data. This is supported by most web browsers and web servers.