Kubernetes WAAP Version 1.14.0
This version includes the following new capabilities:
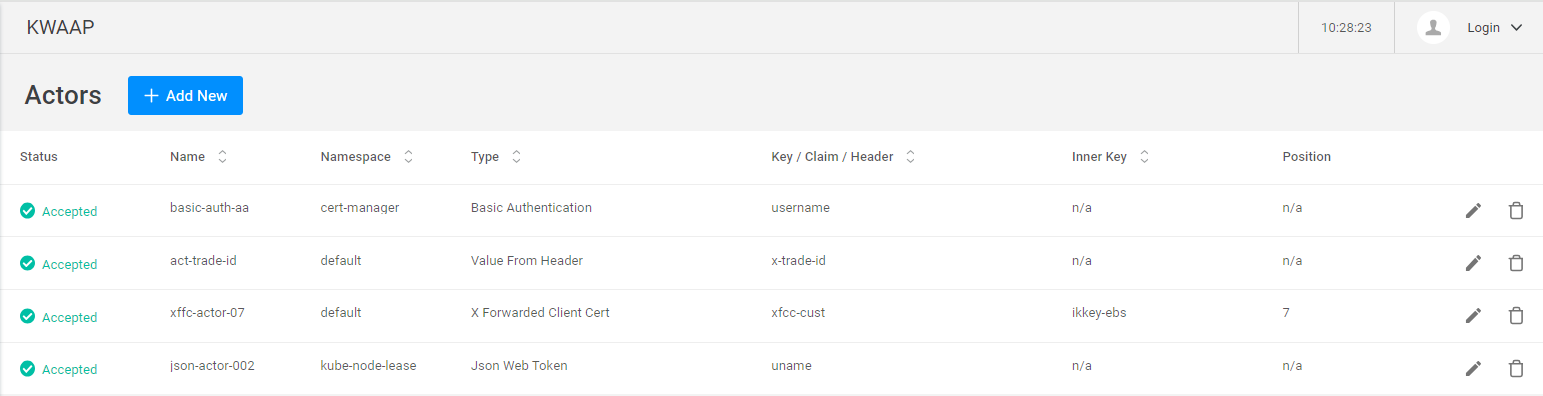
Actors Analysis
Actor Analysis introduces flexible rate limiting and attack scoring options based on the definition of an Actor. It allows defining rate limits and assigning violation ratings using various Actor identification methods. As such, Actor Analysis provides robust protection against web and API attacks. This feature offers:
 Fine-grained Rate Limiting
Fine-grained Rate Limiting—By enabling rate limiting based on different Actor ID formats, you can effectively control and limit the activity of specific Actors within your application. This prevents excessive requests or abusive behavior from impacting your infrastructure, and helps ensure fair resource allocation.
 Enhanced Attack Scoring
Enhanced Attack Scoring—Assigning violation ratings to specific Actors permits differentiating between legitimate and malicious activities more accurately. It takes into account information such as the client IP, application ID, and user ID. Doing so, KWAAP can score and mitigate potential threats precisely.
 Flexible Application Architecture
Flexible Application Architecture—Multiple Actor ID format support allows seamless integration with various authentication mechanisms and application architectures. It accommodates diverse use cases and ensures compatibility with a wide range of environments. The Actor ID formats include:

Value from HTTP Header
The actor ID is located in an HTTP header used by your application. You can specify the header name and configure KWAAP to extract the actor ID from the header value. This approach is useful when your application utilizes a custom token or identifier to represent the client. A common API use case is when the traffic is authorized based on a header that includes an API Key.

Basic Authorization
When using Basic Authentication, the Actor ID can be extracted from the base64-encoded Authorization header. KWAAP decodes the header value, extracts the username, and defines it as the Actor ID for rate limiting or violation rating purposes.

JSON Web Token
If the application relies on JWT (JSON Web Token) authentication, KWAAP can leverage an Actor ID present in the JWT claims. The Actor ID can be the JWT token ID (JTI) itself, a user ID, a group ID, or any other relevant identifier contained within the JWT claims.

x-forwarded-client certificate
The x-forwarded-client certificate option allows extracting the Actor's ID from the client certificate sent in an HTTP header. This method is useful because client certificates contain information that uniquely identifies the client.
With all capabilities considered, Actor Analysis provides protection against various web and API attacks, including but not limited to:
 User-based rate limiting and protection against application-level DDoS attacks
User-based rate limiting and protection against application-level DDoS attacks User enumeration attacks
User enumeration attacks API abuse and excessive usage
API abuse and excessive usage Session hijacking attempts
Session hijacking attempts Brute force attacks
Brute force attacksForensics Security Events
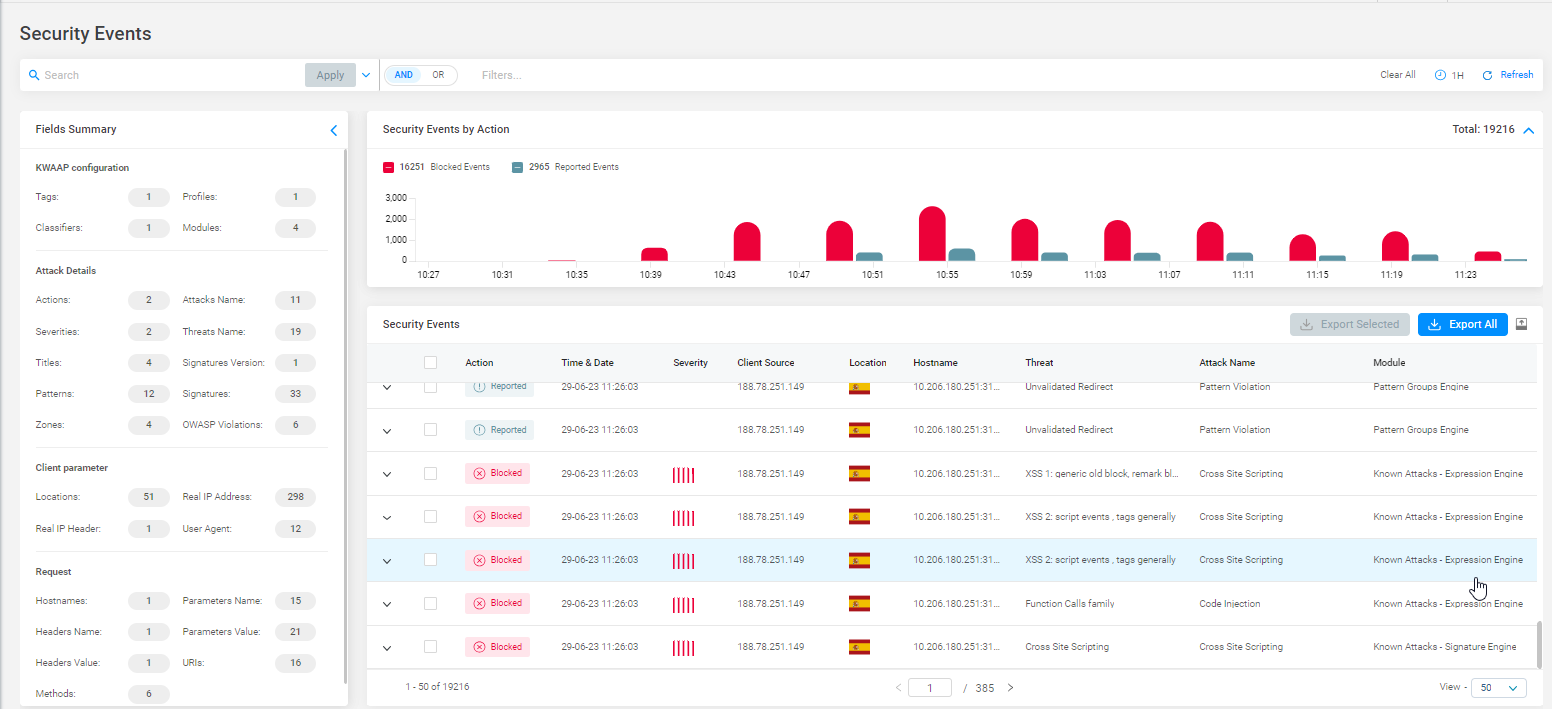
We introduce an advanced feature that enhances the way you troubleshoot security events. With our new Forensics Security Events functionality, you can now easily investigate and analyze security events in a more user-friendly way. As such, this enables you to take proactive measures against potential threats. The key capabilities and options available are:
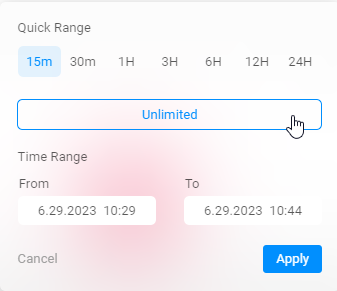
 Time Selection
Time Selection—You have the flexibility to choose the desired time frame for analyzing security events. You can select a specific date range or a custom time interval to focus on the relevant period.
 Compact View or Detailed View
Compact View or Detailed View—Based on your preference, you can customize the way to display security events. You can opt between a compact view for a quick overview, or detailed view of comprehensive information about each event.
 Filters Option
Filters Option—With powerful filtering capabilities, you can apply filters to any available field to narrow down the results and thus allowing you to focus on specific aspects of security events.
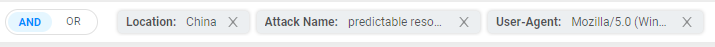
 AND/OR Conditions
AND/OR Conditions—To refine your search even further, you can apply advanced filtering logic using AND/OR conditions between different fields. This allows for more precise filtering based on complex criteria.
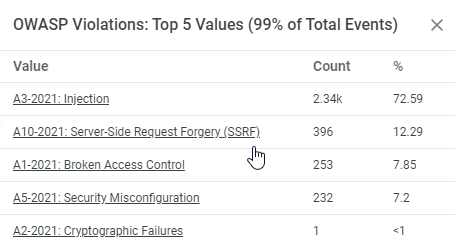
 Top 5 Values
Top 5 Values—For the selected time frame, you can easily identify the most significant trends and patterns by viewing the top 5 values for each available field. It displays the count and percentage of occurrence of each value. With this capability, you are able to quickly identify the most prominent security events and click to refine the view based on the top 5 values.
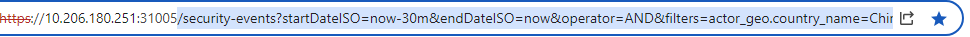
 Query Parameters and Bookmarking
Query Parameters and Bookmarking—This capability aims at the importance of maintaining context and being able to easily revisit specific selections. It stores the selected filters in the query parameters so that you can bookmark your search criteria. This makes it effortless for you to return to previous analyses, maintain a consistent workflow, and offer an option to facilitate sharing your filter criteria with others.
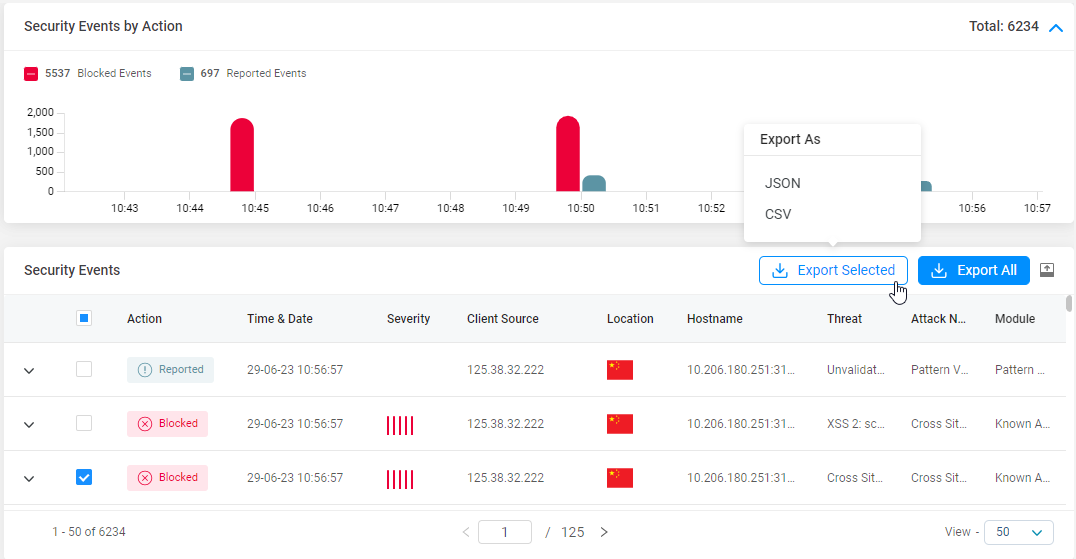
 Export Options
Export Options—To facilitate further analysis or sharing of data, you can export security events in both CSV and JSON formats. You have the flexibility to export all events or select specific ones based on your requirements.
With these advanced capabilities, you can drill down into security events, accurately investigate potential threats, gain a deeper understanding of attack patterns, identify false positives, and refine their security policies—all from a single intuitive screen. The Forensics Security Events feature allows you to proactively manage your security posture and make informed decisions to protect your systems and data.