Kubernetes WAF Version 1.10.0
This version includes the following new capabilities:
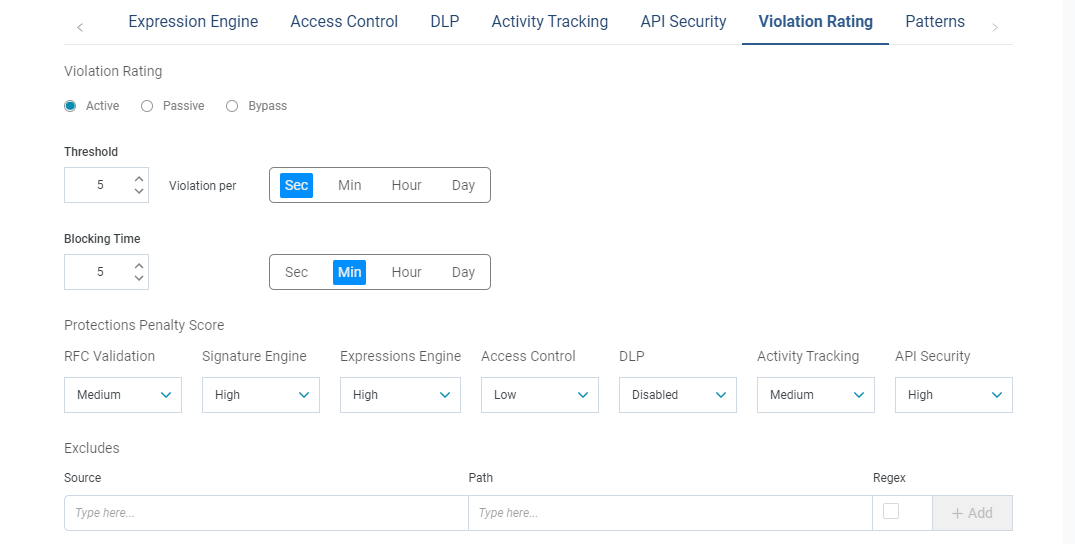
Violation Rating
Violation Rating is a new Protector. It analyzes the behavior of a source to identify suspicious behavior, and aggregates violations for a defined set of protections.
In the configuration, per Classifier, each protection module scores the attack violation with a penalty score, Low (1), Medium (3), High (5), or Disabled (0).
The violation score is counted for each source and is valid for a configurable period of time.
When the Total Counted Score passes a threshold, the actor is blocked for a configurable period of time.
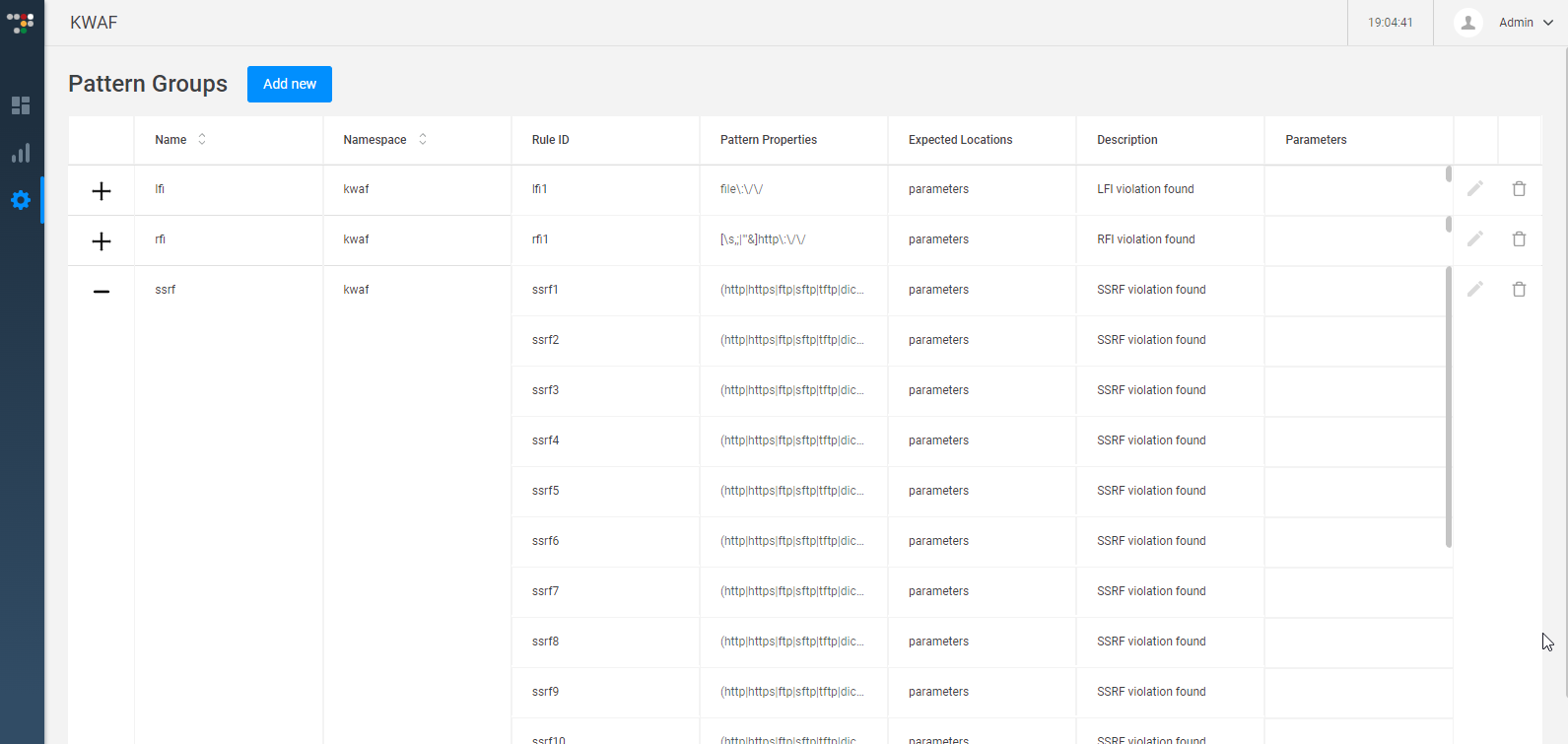
Pattern Group
Patter Group is a new Protector. It allows you to create a protection from a family of attacks.
You can define multiple Custom Rules and group the rules under a Pattern Group.
By default, three Pattern Groups exist: LFI, RFI and SSRF.
You can add/delete rules in the group. The definition of a rule is similar to a Custom Pattern.
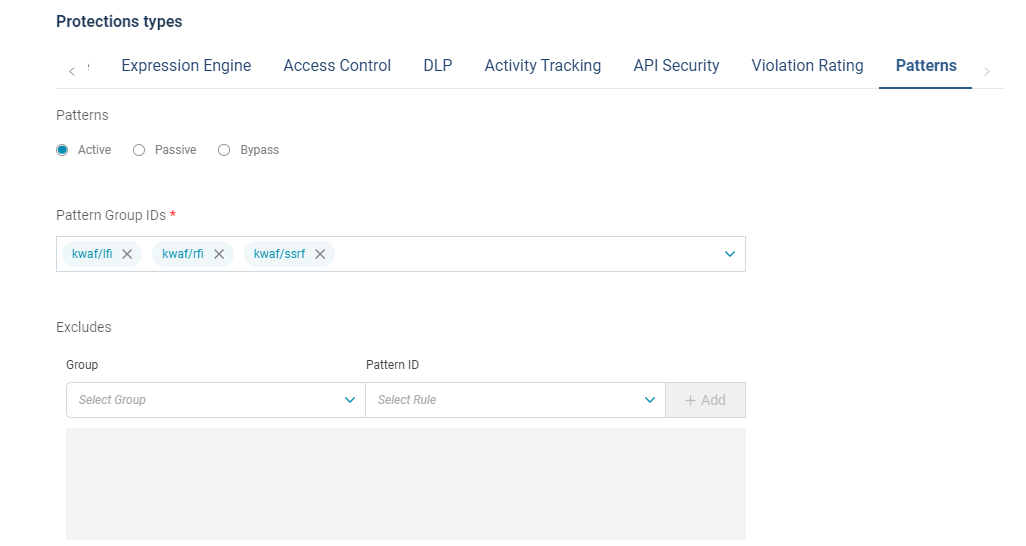
In the Protector configuration, you can choose which Patter Group to activate in the specific Classifier.
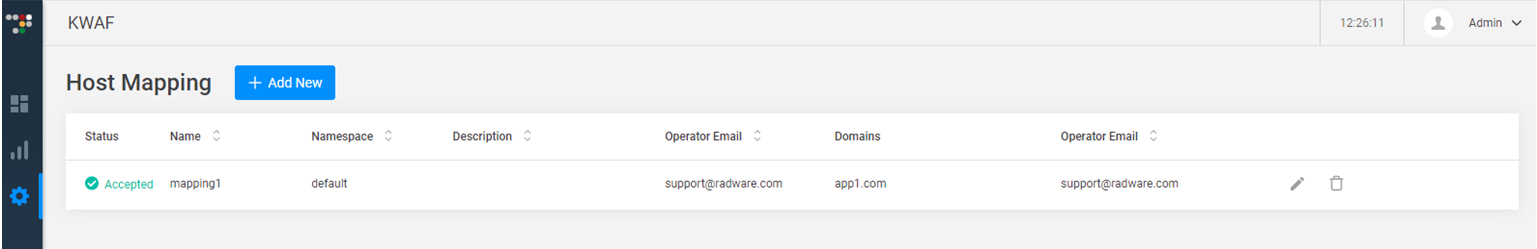
Host Mapping
Host Mapping provides a way to have a single security policy comprised of multiple Profiles.
The Mapping is a list of maps binding hostname groups with profiles, so that each Profile contains the security policy for the hostname group.
The Mapping consists of associating Domain name (protected servers) to a Profile (Security Profile).
Each Profile contains one or multiple Classifiers (rule to classify the traffic) and each Classifiers contains the Protectors configuration (Security module configuration).
Profile Dashboard
The Profile dashboard provides a dashboard-style overview (similar to the System Overview dashboard) for each individual Profile.
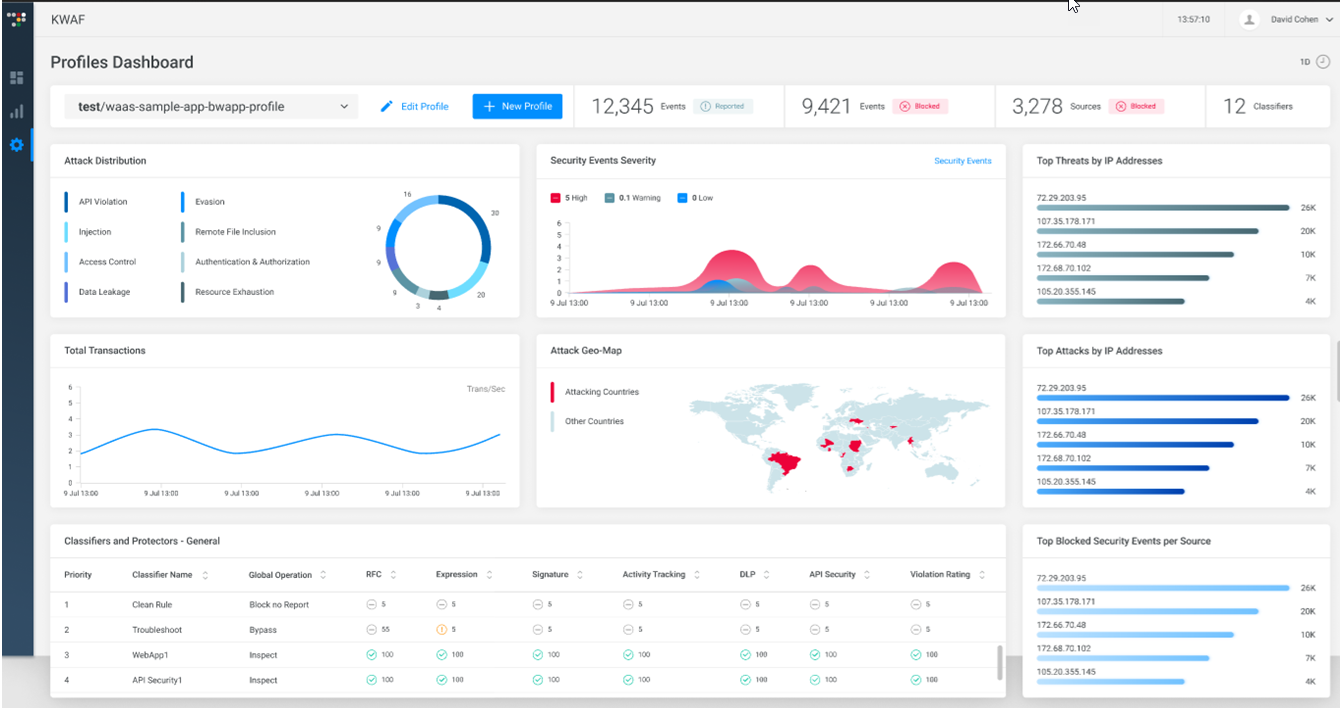
The Profiles dashboard includes the following widgets:
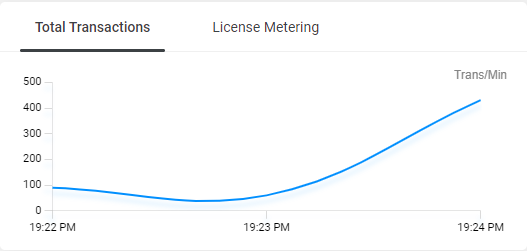
License Metering Widget
In the System Overview dashboard, a License Metering widget allows you to extract and view license data on the dashboard.
License metering shows you the number of transactions (attacks) per profile per a time range (for example, the last 30 minutes).
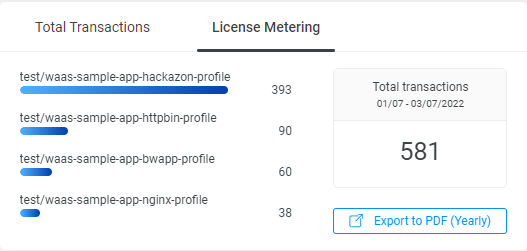
The License Metering data can be exported to a PDF file that presets the transactions per month over the last year.
API Security
A new “Block” action for the endpoint’s schema enforcement is added.
Previously, “Active”, “Passive” and “Bypass” actions were supported (for each endpoint). The new "Block" action immediately blocks the client request. It manages use cases such as:
HTTP/2 Support
HTTP/2 protocol is supported end-to-end, including Security Inspection.