Kubernetes WAF Version 1.6.0
This version includes the following new capabilities:
KWAF Backend Communication
Starting with KWAF version 1.6.0, all KWAF back-end communication is mTLS encrypted.
XML Support
As part of the RFC Validation protection, the module parses and evaluates the XML body structure of requests as well as values encapsulated within the XML tags. Parameter names are created using the full hierarchy of nested tags containing each value.
Specific XML security violations, such as XML Bomb attacks and XXE attacks, will be mitigated and/or reported based on the operational mode of the RFC Validation protection.
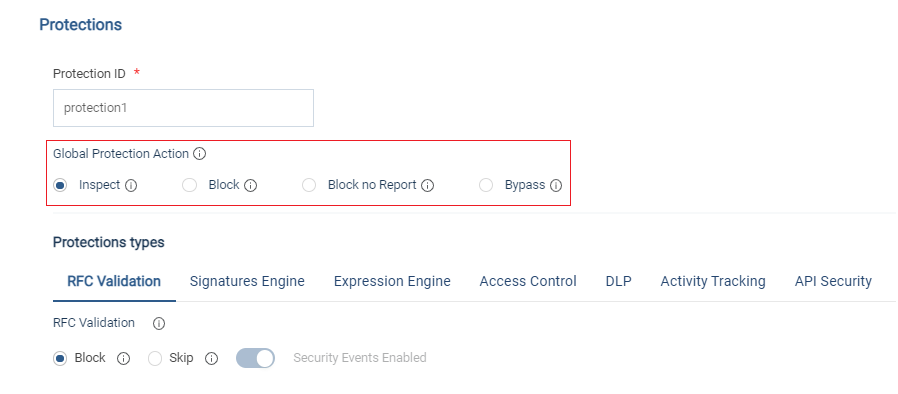
Classifier Global Protection Mode
Classifiers define attributes to match against the client traffic (Application Path, particular HTTP header value) and assign protections to this traffic. Classifiers allows flexible configuration of protections based on traffic attributes per policy.
Per classifiers, we can add a Global Protection mode before it reaches the protection modules:
Exclusion Rules
Depending on the nature of the API/Web Application traffic, the rule IDs defined in the Expression engine, or the Signature engine can be excluded (false positive for example).
The scope of the exclusion is global within the given classifier. The exclusion can now be limited to the parameters and headers of the request:
For the Expression engine, the exclusions can be:
Exclude from Classifier: | 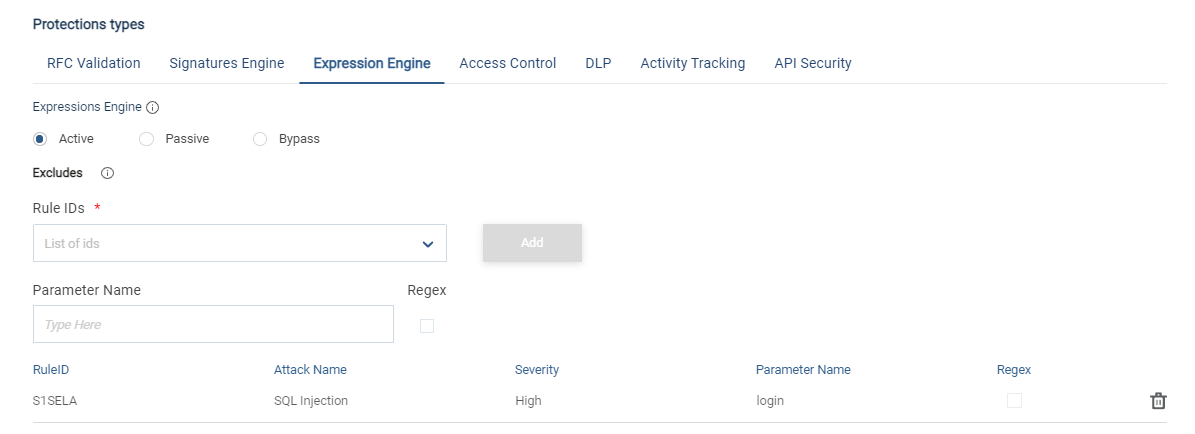 |
Exclude from Forensics: | 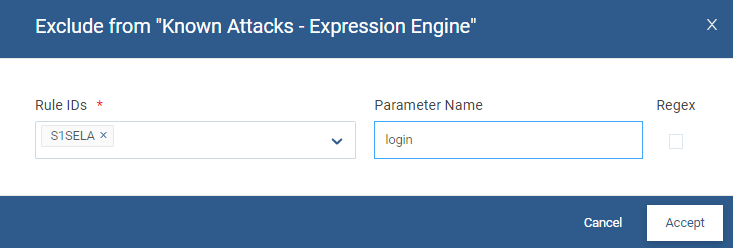 |
For the Signature engine, the exclusions can be:
Exclude from Classifier: | 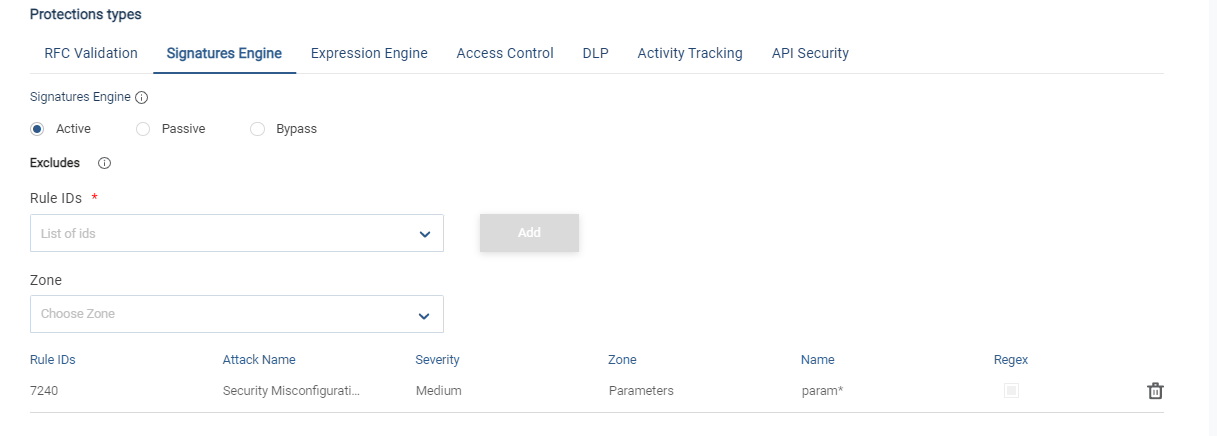 |
Exclude from Forensics: | 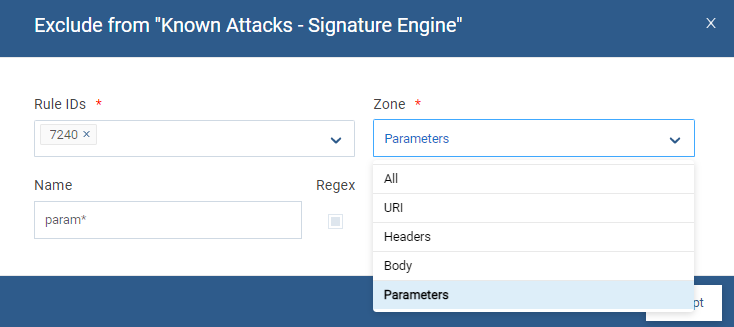 |
Latency
In an Istio environment, using the Envoy external authorization filter, the following metrics help to measure the latency at different levels:
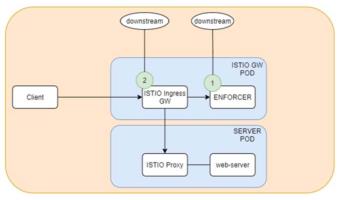
The metrics can be collected from Grafana and exposed in a dashboard, as shown in the example below:
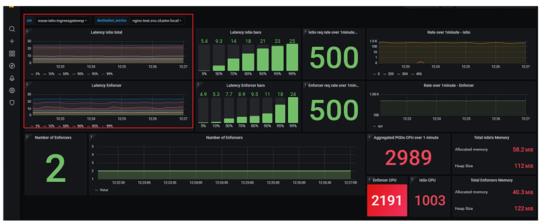
Bug Fixes and Improvements
This version includes the following fixes and improvements: