Kubernetes WAAP Version 1.15.0
This version includes the following modifications:
API Quota
API Quota is a feature that enables defining limits on the number of API requests that you can make to a specific API endpoint and method within a defined time frame. You can configure both the duration and units of these limits. For example, setting a limit of four requests per day or 950 requests per second.
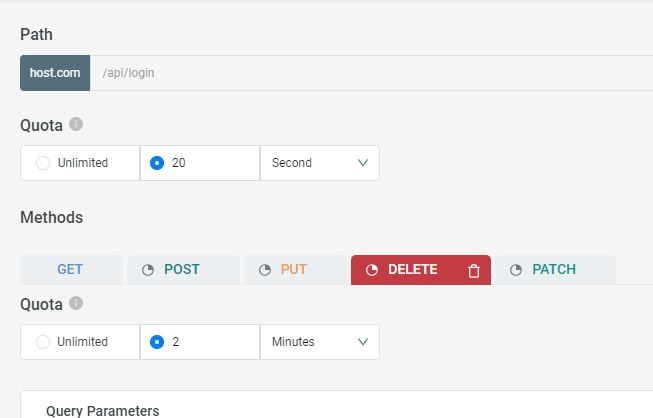
The value of API Quota resides in its capacity to control and optimize API usage. Some of the reasons for its value include:
Quota is available as an extension in the OpenAPI file. It means that you can import it within the API definition and update it from the KWAAP GUI, or manually with a Patch mechanism (refer to the User Guide for more details).
Pattern Operation Mode
In the current implementation of Pattern Protection, the functionality offers the concept of custom signature groups, which essentially forms families of specific security rules. As a default setup, there are predefined groups for LFI (Local File Inclusion), RFI (Remote File Inclusion), and SSRF (Server-Side Request Forgery).
In this latest version, a significant enhancement has now been introduced. It allows for the specification of a distinct operation mode for each of these custom signature groups. This means that while Pattern Protection can be set either globally in Passive (report-only) or Active (block and report) mode, individual groups within it can have their own unique operation mode settings.
For instance, if the global Pattern Protection is configured in Passive mode, you can selectively set one or more custom signature groups to operate in Active mode, which means that they actively block and report malicious requests. Conversely, if Pattern Protection is globally set to Active mode, you can configure specific groups to function in Passive mode, where they only report on requests without taking immediate blocking actions.
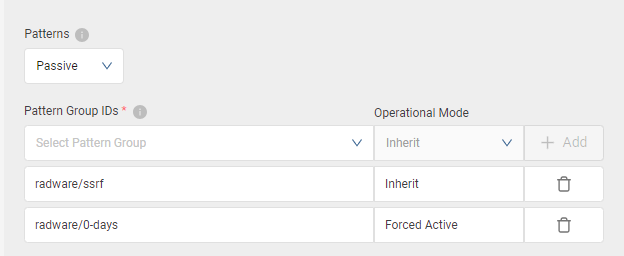
The ability to define specific operation modes for custom signature groups within Pattern Protection brings several key advantages:
In summary, the ability to define operation modes for custom signature groups in Pattern Protection enhances security, optimizes resource usage, and provides the capability to respond effectively to a wide range of security challenges. This fine-tuned control is a valuable asset for maintaining a robust and adaptable security infrastructure.
Cookie Actor
Following the introduction of Actor Analysis, we have incorporated a new feature in this release that allows the creation of an Actor based on a cookie value. This enhancement is particularly valuable for numerous organizations that utilize cookies to establish various parameters, such as directing requests or monitoring user activities through session cookies.
For instance, cookies may encompass details such as the:
By designating a cookie as an actor, you can achieve highly precise rate limit detection, enabling more granular tracking of client and server behaviors within the context of both the client and the application.
Kong Gateway Integration
Incorporating Kong Gateway into our product is a significant advancement. It broadens KWAAP compatibility, strengthens security, and ensures smooth integration within the API landscape. It enables KWAAP to extensively protect API traffic in a variety of environments.
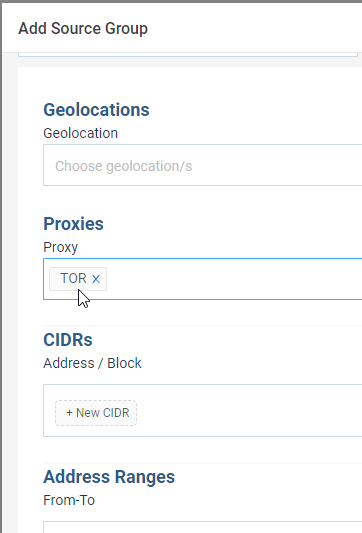
Tor Exit Node
In our recent update, a significant enhancement to the Source Group definition has been introduced. Specifically, a new category of source types known as Proxy, which encompasses Tor Exit Nodes IPs, has been added.
This addition provides several advantages:
Metrics
In our latest update, the product has been enriched with an array of new metrics. This includes statistics like Total Blocked Requests insights into connection stability with Connection Error, performance monitoring with Enforcer Response Time, and version tracking such as Signatures Version. For detailed explanations and utilization guidance to empower your system optimization and security management, refer to the User Guide.
Internal Elastic Configuration
We offer comprehensive recommendations for configuring the internal Elastic Database to effectively handle Security Events and Access Log Events. Our guidance ensures optimal setup which enables users to harness the full power of KWAAP features for enhanced security monitoring and analysis. Refer to the User Guide for more details.