Kubernetes WAAP Version 1.14.0
This version includes the following modifications:
Nginx LUA integration script
We are thrilled to announce the release of an updated version of our LUA integration script for Nginx. This enhanced script provides customers with a range of options to optimize their configuration based on their specific use cases and requirements. Here is an overview of the key features and options available:
Similar to the functionality offered by Envoy, our LUA integration script now supports buffered requests for inspection. This enables efficient analysis and processing of requests within the Nginx environment.
In scenarios where latency is critical and traffic volume does not allow for a buffered solution, our script offers advanced configuration options for "streamline inspection." This memory-optimized approach ensures efficient inspection in Cloud Edge deployments and other environments where low latency is essential.
For traditional use cases, our LUA script supports a classic blocking mode where the script waits for the KWAAP inspection analysis to be completed before sending the request to the upstream. This ensures thorough inspection and analysis of incoming requests.
The updated script introduces a shadow mode feature where a copy of the traffic is sent for analysis, while the incoming request is immediately forwarded to the upstream server. This allows for real-time analysis and minimizes impact on request processing.
Customers have the flexibility to choose between inspecting partial or full requests based on their specific needs. This ensures that the inspection process is tailored to their desired level of coverage.
To provide customers with control over the behavior of the script in case of inspection failures or errors, our LUA integration script supports both fail-open and fail-close options. This allows them to define the desired response when inspection cannot be completed successfully.
Our script offers fine-grained control over the latency associated with inspection operations. Customers can configure and optimize the sending, receiving, and reading of request/response data, aligning the script's performance with their specific requirements.
With this comprehensive range of options, customers can fully customize the LUA configuration based on their unique use cases, whether it is Cloud Edge deployment, classic reverse proxy setups, API gateway integration, ingress gateway integration, microservice integration, and more. This empowers customers to strike the right balance between performance and security coverage, ensuring optimal protection for their applications and systems.
It is a powerful tool that optimizes the Nginx deployments offering a configuration balance between level of performance and level of security coverage.
OWASP WEB event classification
On top of the new Forensics Security Event screen, a new field called "OWASP” is available. This field maps each security event to the OWASP WEB 2021 categories, providing valuable insights into the specific vulnerabilities and attack vectors associated with each event.
The OWASP classification helps to gain a deeper understanding of the nature of security incidents, enables more targeted analysis and response and enhances overall web application security posture.
Header inspection
Related to HTTP Header inspection, KWAAP now supports Base64 decoding and validation. This means that any Base64-encoded value in headers will be automatically decoded (once or multiple) and analyzed for potential security risks. This helps uncover any malicious content or attempts to exploit vulnerabilities through manipulated headers.
Furthermore, our header inspection also addresses parameter pollution attacks. Parameter pollution attacks occur when multiple instances of the same header are included in a request, potentially leading to confusion or bypassing of security measures. Our solution detects and mitigates such attacks, ensuring that only valid and properly formatted headers are processed.
KWAAP Cookie Classifier
On top of the current option to configure the KWAAP classifier, we can now configure the Classifier with one or multiple pairs of Cookie Name/Cookie Value.
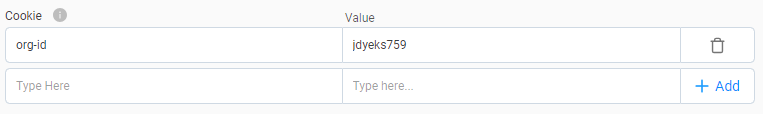
Cookies play a crucial role in WEB and API applications, often used for session management, user identification, tenant identification in a multi-tenant application, server instance identification and other important functionalities. With the ability to configure the classifier with specific Cookie Name/Cookie Value pairs, you can now tailor the security policy to match the unique requirements of the environment and/or the applications.
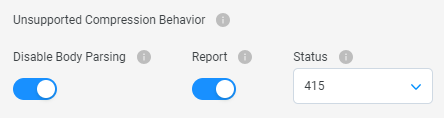
Client Request Compression
We added in the KWAAP RFC module the option to handle compression in client requests. These options are designed to cater to various scenarios where compression support may not be available or desired.
Rate-limiter feature change
The existing features in the KWAAP rate-limiter module, Activity Tracking and Violation Rating, have been enhanced for even better functionality. These features are designed to help you monitor and evaluate client requests, enabling you to track activity levels and identify potential attacks.
From this version, it is important to note that whenever any aspect of the KWAAP configuration changes, such as adjusting rate limits or modifying settings related to activity tracking and violation rating, the counters associated with these features will be reset. This ensures that the metrics accurately reflect the updated configuration and provide reliable data for analysis.