What’s CHANGED in 32.4.0.0
HTTP/2 Proxy General Availability
The full HTTP/2 Proxy capability that allows load balancing HTTP/2 traffic to HTTP/2 real servers, is now Generally Available (it was previously available as Beta only).
The following capabilities are supported for HTTP/2 Proxy:
To configure HTTP/2 Gateway for a virtual service:
1. Define the HTTP/2 policy, as follows:
a. Select Configuration > Application Delivery > Application Services > HTTP. HTTP/2.
b. In the Policy table, click + to add an entry. The relevant Add tab displays.
c. Click Enable HTTP/2 Policy to enable the policy, once defined.
d. In the Policy ID field, enter an ID for the new policy.
e. In the Backend tab, select Backend HTTP/2 to enable HTTP/2 proxy.
f. Click Submit.
2. Define the required HTTPS virtual service, including an SSL Policy. The server group used for this service must use the HTTP/2 health check. Predefined clear text (h2c) and SSL (h2) HTTP/2 health checks are available.
3. In the virtual service HTTP tab, select the HTTP/2 policy to use with this service.
Alteon VA Enhancements
Support for Mellanox CX5 Alteon VA over VMware
Mellanox CX5 100G NICs are supported on the Alteon VA running VMware in pci pass-through mode.
Improved Performance on AWS
The performance of Alteon VA running on AWS was improved by supporting SRIOV on AWS.
Alteon VA, when running on AWS instances, supports SRIOV (enhanced network) reaching 10 Gbps (such as m4.10xlarge can reach 10 Gbps L4 throughput).
By running Alteon VA on instances supporting SRIOV (enhanced networking), the Layer 7 and SSL performance can be significantly improved utilizing the Alteon DPDK capabilities to run multiple SPs using the Alteon TDVA.
Extended GEL Throughput Points
The granularity of the Alteon instances running a GEL instance was extended.
Alteon instances running GEL license can now be assigned the following throughput points:
Layer 7 Performance Improvement
Layer 7 performance (L7 RPS, L7 BW, and SSL bulk encryption) of the following Alteon platforms has been improved:
The new tech spec includes the updated numbers. You can find it on Radware portal or Radware official Web site.
Note: The improvement takes effect only when Layer 4 HW hash is enabled.
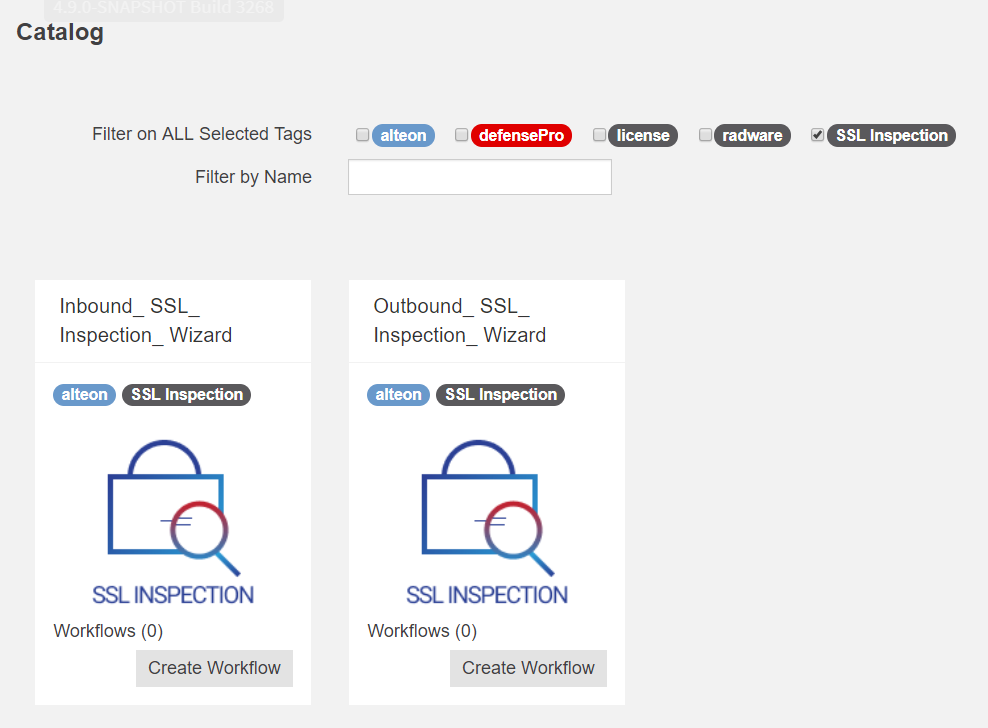
SSL Inspection Wizard Enhancement (vDirect Based)
An updated wizard for quick and easy configuration of an outbound SSL Inspection solution is now available using vDirect workflow version 1.1.0-1 available on APSolute Vision 4.30.
The updated wizard provides full-transparent deployment (where Alteon acts as bump-in-the-wire) on top of the Layer 3 deployment which was available in workflow version 1.0.0.
Notes:
To access the wizard, access vDirect from APSolute Vision, navigate to the catalog, and filter by SSL inspection:
Management Login Using the SSH key
In addition to the basic user/password authentication, Alteon also supports SSH public key authentication. Public key authentication improves security considerably as it frees users from remembering complicated passwords (or worse, writing them down). It also provides cryptographic strength that even extremely long passwords cannot offer.
SSH public key authentication offers usability benefits as it allows users to implement single sign-on across the SSH servers they connect to. Public key authentication also allows for an automated, password-less login that is a key enabler for the countless secure automation processes.
Note: SSH public key authentication support is available only for local users.
NFR ID: prod00235977
AppWall
The Geolocation database and IP Groups now support IPv6 addresses and can be used in Web User Roles.
Application Dashboard and Basic Analytics License Enforcement
Starting with this version, Alteon basic analytic (metric-based reporting) requires the Perform package license.
Note: The Application dashboard is available in APSolute Vision, and is also based on Alteon basic analytics capabilities. Ensure that the Alteon devices for which you require application dashboard monitoring are installed with the Perform package.
Virtual Service Traffic Event Logs Additions
In addition to the HTTP, SSL, and Layer 4 connection separated events, Alteon now also supports Unified events.
Using Unified events, an event is sent per transaction including HTTP, SSL, and Layer 4 information during the same event, allowing easier integration with third-party SIEM products (like ELK or Splunk)
Unified events also identify two types of events:
Notes: