What’s New in 32.4.0.0
This section describes the new features and components introduced in this version on top of Alteon version 32.4.0.0.
For more details on all features described here, see the Alteon Application Guide and the Alteon Command Reference for AlteonOS version 32.4.0.0.
Documentation in HTML Format
Starting with this version, the documentation set is available from the Radware Customer Portal in both PDF and HTML format. You can access the new HTML documentation either from the Documentation Download page for a given version, or you can perform a search for text from the Customer Portal search feature.
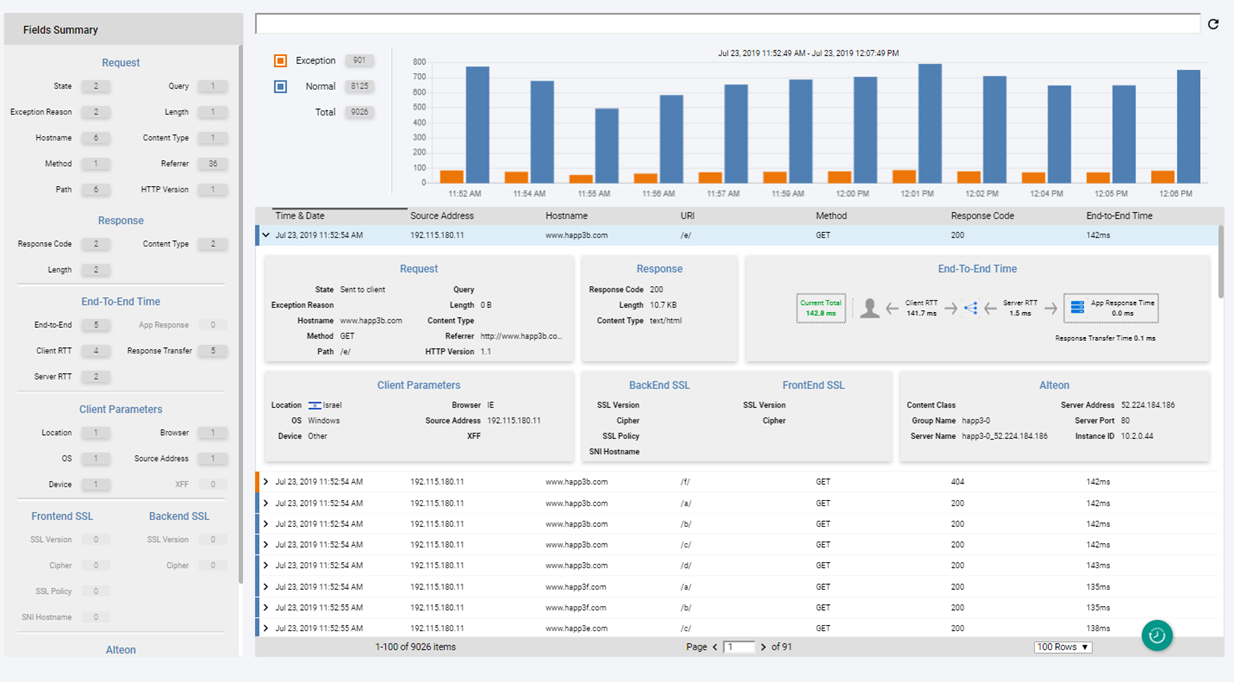
Application Traffic Log Dashboard (Advanced Analytics)
The Application Traffic Log dashboard is available starting with this version, using APSolute Vision version 4.30 or later.
It provides deep-level analytics based on transaction information, improves troubleshooting and speeds up the root cause analysis, it provides user insights, and enables anomaly detection.
Using the Traffic Log dashboard, you get clear insights to the traffic patterns that your application handles.
The dashboard includes the following components:
Exception events can quickly be identified, including:
Notes:
WAF Support in Standalone Form-Factor
Integrated AppWall is now also available on Alteon platforms running in Standalone mode. This includes the following platforms: 4208 /S, 5208 /S, 5424 S/SL, 5820 S/SL, 6024 /S/SL/FIPS 7220, 7612.
To provision these capabilities on a Standalone model, perform the following steps:
1. Install the appropriate AppWall licenses on the Alteon platform.
2. Allocate the appropriate number of cores for AppWall. Note that device reset is required to activate core allocation to AppWall.
Note: When boot configuration is set to factory default, the device reboot removes the allocated AppWall cores.
Single IP Support on Common Alteon VA Environments
Starting with version 32.4, the option to run Alteon VA in single IP mode is available on AWS, VMware, and KVM on top of its current availability in Azure.
Single IP mode is automatically selected when an Alteon VA has a single NIC attached to it.
Configuring an Alteon VA running in single IP mode is very straightforward, as VIPs, PIPs, and interface configuration are done automatically behind the scenes.
There are also cases of public clouds that provide instances with only a single NIC, and using this capability enables the support of such environments.
SCTP Support
The Stream Control Transmission Protocol (SCTP) is a Transport Layer protocol, serving in a similar role to the popular protocols Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). SCTP is a reliable transport protocol operating on top of a potentially unreliable connectionless packet service such as IP. It offers acknowledged error-free non-duplicated transfer of datagrams (messages). Detection of data corruption, loss of data and duplication of data is achieved by using checksums and sequence numbers. A selective retransmission mechanism is applied to correct loss or corruption of data.
The decisive difference from TCP is multi-homing and the concept of several streams within a connection. In TCP, a stream is referred to as a sequence of bytes, but in a SCTP, a stream represents a sequence of messages (and these may be very short or long).
Radware defines a single-home SCTP association as a connection between two single IP addresses. A multi-home SCTP association is a connection between multiple addresses. Both client and server can supply additional addresses on top of the one that is carried in the Layer 3 header.
The client sends the additional IP addresses in the INIT packet while the server sends the additional IP addresses in the INIT-ACK packet.
When NAT is performed for SCTP, the INIT and INIT-ACK packets should be updated and the SCTP association should be supported.
SCTP Load Balancing with Alteon
Alteon now supports Layer 4 load balancing for SCTP. The following SCTP communication types are supported:
New Alteon Platforms (Alteon D-5424/D-5820)
The Alteon Application Switch D-5424/D-5820 is a very high port density ADC with up to 40 Gbps throughput.

These platforms support the latest encryption standards (ECC) with an HW SSL acceleration integrated by default, and have superior performance coupled with a wide range of connectivity options, high performing and reliable storage (SSD), high memory size, advanced capabilities, and OnDemand scalability.
They are suitable for small to medium-sized enterprises that require a high-performing solution.
Alteon D-5424/ D-5820 Highlights
Notes:
SSL
SNI-based Decisions without SSL Decryption
There are scenarios that require making host-based decisions for SSL traffic without decrypting it using the Server Name Indicator (SNI). Previously, this capability was available only for outbound SSL Inspection. Starting with this version, this was extended to support the following scenarios:
a. Configure a front-end filter that handles bypassed hosts, using an SSL Content Class to match the hosts that should be bypassed, and no SSL policy.
b. Configure additional front-end filter/s that handle traffic that must be inspected with an SSL policy and the necessary certificate/certificate group.
c. Configure a Multi-protocol Filter Set and attach to it the front-end filters.
a. Configure an SSL Content Class that matches the hostnames for which you want to define a certain policy (for example, Office365 hostnames) or a URL Filter policy that matches the categories for which you want to define the policy.
b. Configure SSL Content Class that includes a single Host entry set to “.” – this matches all the rest of the SSL traffic (“any”).
c. Configure filter SSL (Application set to HTTP) and attach to it the SSL Content Class or URL Filter Policy that matches the specific hosts/web categories. If it is a URL Filter Policy, the URL Filtering Mode must also be set to SSL.
d. Configure an additional SSL filter (Application set to HTTP) that handles the rest of the SSL traffic and attach to it the “any” SSL Content Class.
e. Configure a Multi-protocol Filter Set and attach to it the above filters. Note that the above filters do not include an SSL policy.
a. Configure SSL Content Classes that match the hostnames you want to redirect.
b. Configure Content Rules and attach them to an HTTPS/SSL virtual service.
Notes:
OpenSSL Update
The OpenSSL version is updated in this release as follows:
AppWall–- Redirect Validation
Remote File Inclusion (RFI) and Local File Inclusion (LFI) are file inclusion vulnerabilities that allow an attacker to include a file or expose sensitive internal content, usually exploiting “dynamic file inclusion” mechanisms implemented in the application. The vulnerability occurs due to the use of user-supplied input without proper validation.
AppWall’s Redirect Validation scans all parameters in the request (including JSON, URL and body parameters) and looks for external or internal redirect attempts to include files.
You can add trusted domains and trusted URIs for which the Redirect Validation are not applied. These can be added manually by clicking Add in the trusted domains and trusted URIs list.
OCSP Multiple Servers
OCSP multiple servers increase availability by letting you configure a secondary (backup) static OCSP server and by supporting a retry mechanism that prevents OCSP communication failure because of a temporary issue (number of retries is configurable).