What’s New in 33.5.2.0
This section describes the new features and components introduced in this version on top of Alteon version 33.5.1.0.
SecurePath Connector
SecurePath integration is an API-based solution for multi-cloud application security. It provides consistent, high-grade, and comprehensive protection for applications hosted across on-premises, private cloud, and public cloud environments, without losing protection quality or operational efficiency.
Radware’s cloud application security solution can be deployed in API mode and does not interfere with customer communications, providing Web Application protection, API Security, and Bot Manager Protection in a single solution.
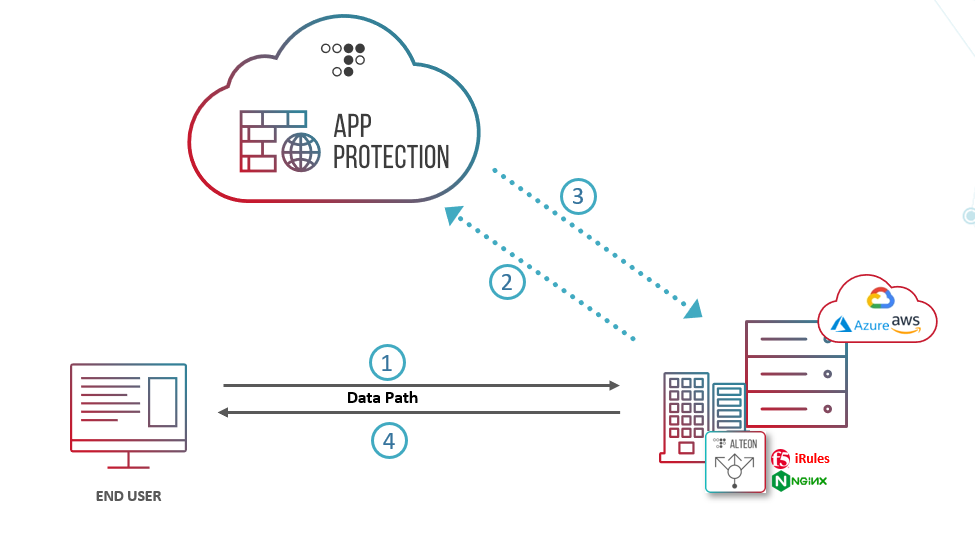
When a client request reaches an application in Alteon which is protected by SecurePath,
1. Alteon sends a copy of the request via the sideband connection to Radware Cloud Security Service endpoint.
2. The Security engine analyzes the data and response to Alteon with the required actions
3. Alteon acts according to the Radware Cloud Security Service response, either allowing the request, blocking it, or challenging the user with a CAPTCHA test.
For the integrated SecurePath to function, you must have at minimum the Perform package, and you must have an license for the required Radware Cloud Security protection (Cloud WAF, BoT Manager).
GEL Management Administrative Modes
Starting with APSolute Vision 5.4, the following administrative modes are available for GEL Management.
AppShape++ Commands
The following AppShape++ commands were added:
Latency Control for Integrated WAF
When the integrated WAF module operates under high loads, inspection of certain transactions can take longer than usual, which translates into longer latency for the client and a less than optimal user experience. There are cases when the customer experience has priority over the application security. To provide a solution for such cases, Alteon now allows forwarding HTTP requests to the server without waiting for the WAF to complete its inspection if the WAF did not answer within a user-defined timeout.
This capability can be enabled at the Secured Web Application (secwa) level by configuring the Timeout parameter (default is 0, meaning the feature is disabled).
Currently, the timeout is applied only for the request part of a transaction. However, if the request times out and is forwarded to the server without WAF inspection, the response of that transaction will bypass the WAF module.
OCSP Health Check
The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate.
The OCSP health check allows monitoring OCSP servers that are load-balanced by Alteon by requesting to validate a user-provided server certificate. The validation request must also include the issuer of the tested certificate (a TrustCA certificate).
The user can decide whether the health check is successful if the OCSP response status is successful irrespective of the certificate status or if the returned certificate status must be “Good”.
The health check supports sending the OCSP request over HTTP or HTTPS, using the POST method.
NFR ID: 211102-000063
Additional SSL Policy Parameters
The following new parameters are now available in SSL policies, for both front-end and back-end SSL:
Note: The Allowed SSL Groups parameter is not available on FIPS platforms (internal HSM card).
Generic HTTP Sideband
A generic HTTP sideband is now supported in virtual services.
With this capability, you can create an HTTP sideband connection to any outside resource, send a custom formatted request, await a response if applicable, act on that response, and so on.
The sideband actions and events are manipulated by an AppShape++ script associated to the sideband.
The sideband actions and events are manipulated by an AppShape++ script associated to the sideband.
If JS injection to the client browser is required as part of the generic HTTP sideband, JS injection must also be enabled on the service (using the /cfg/slb/virt/service/http/jsinject command). This automatically attaches a compression policy to the service to allow for the JS injection functionality.